Finally,
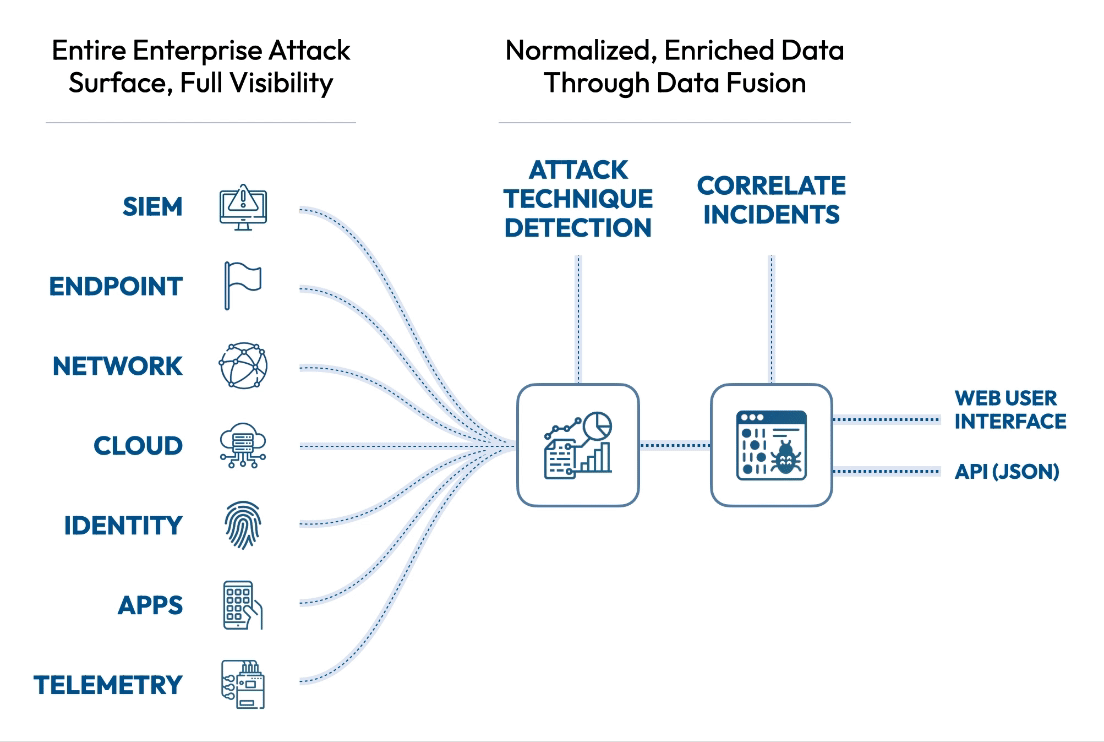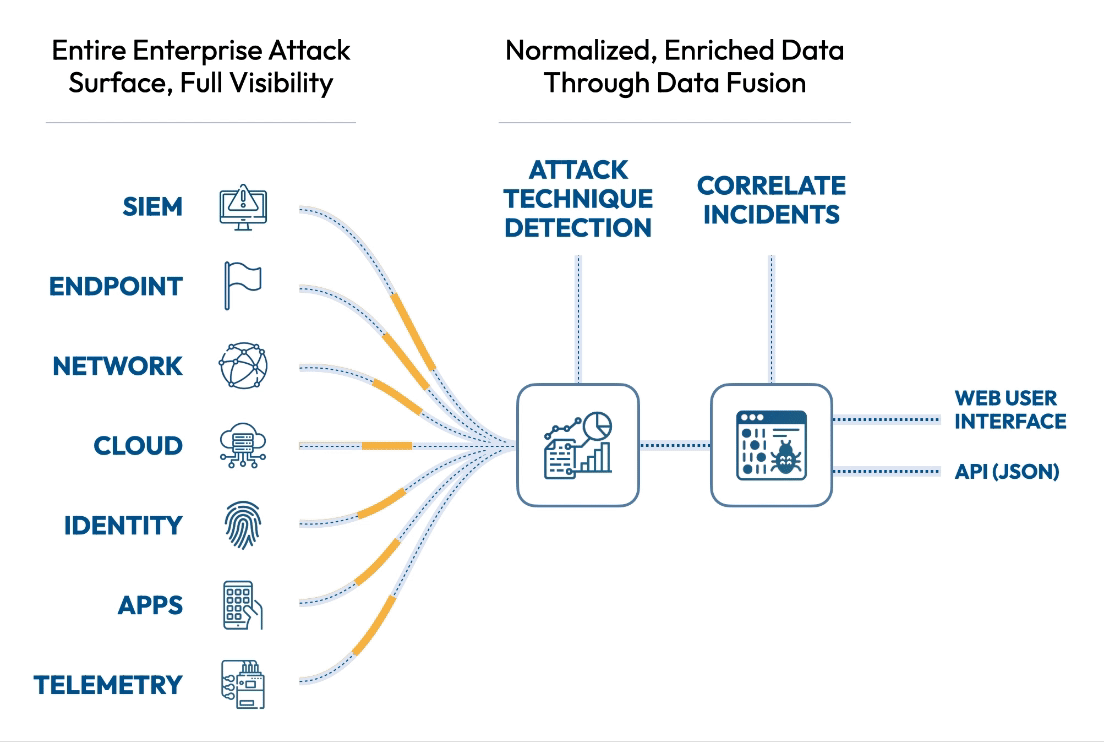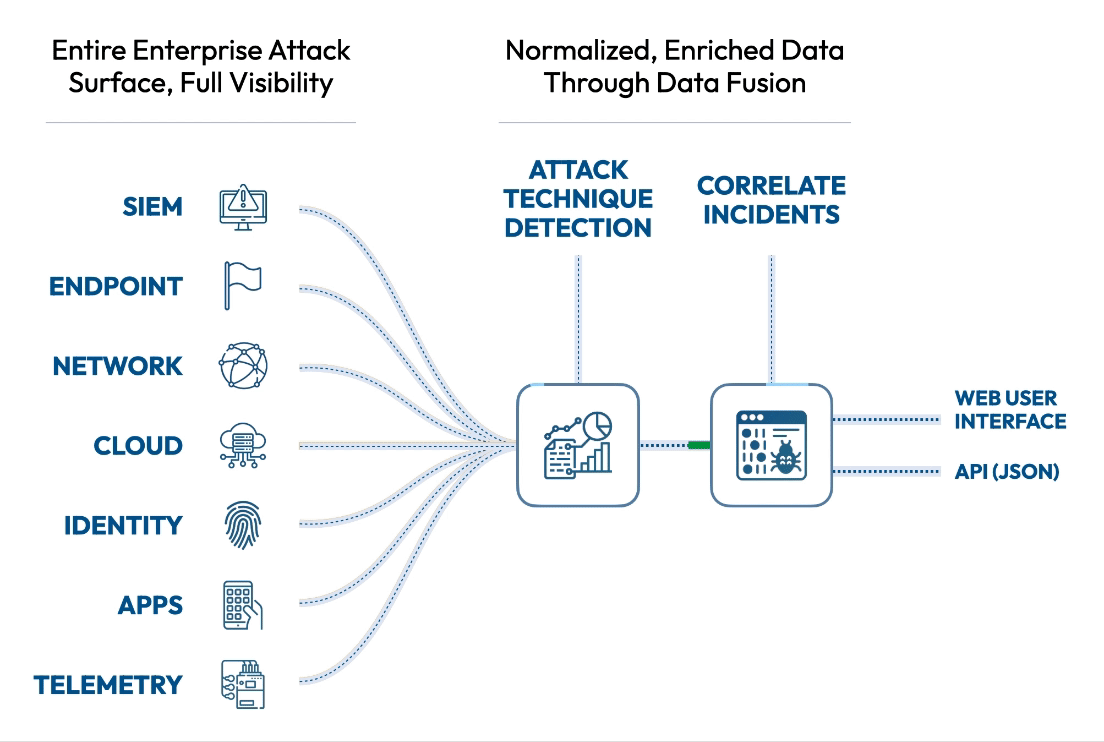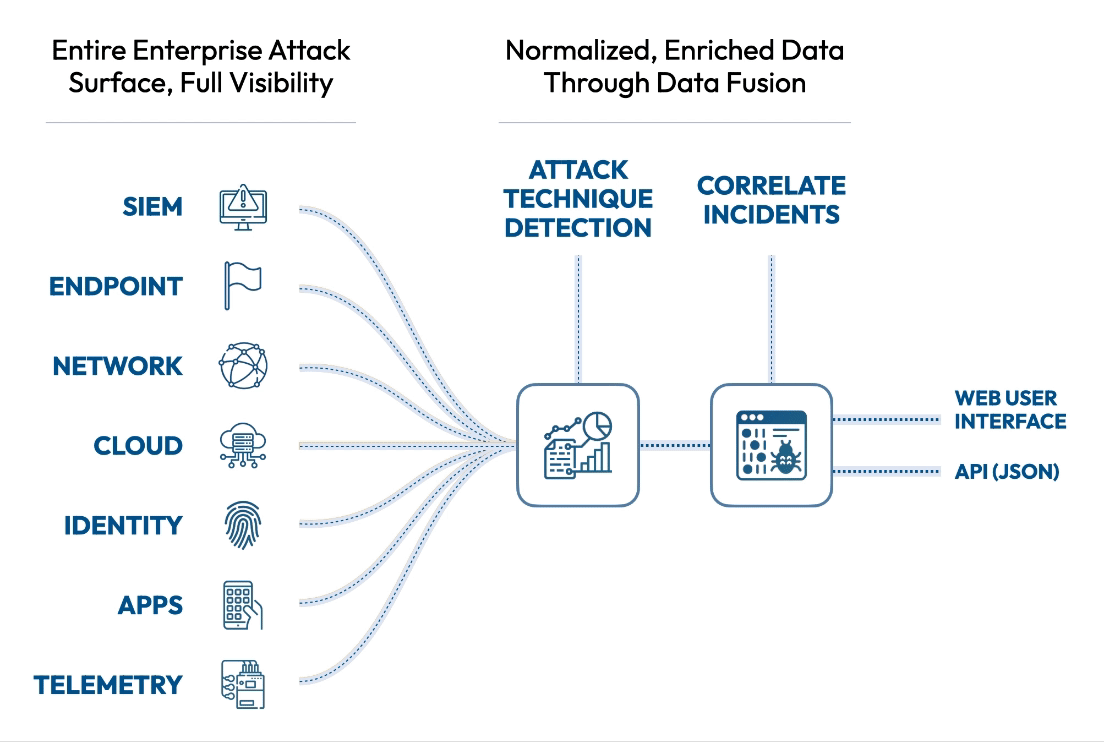
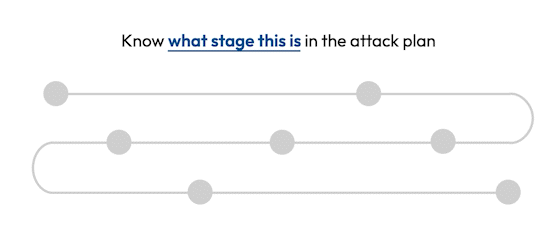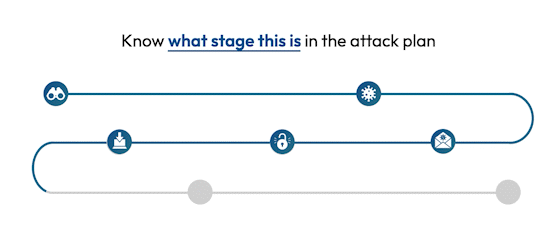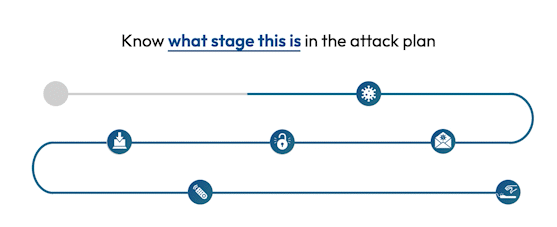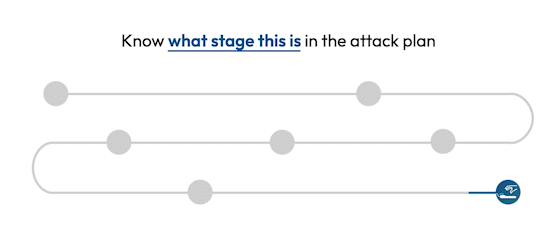
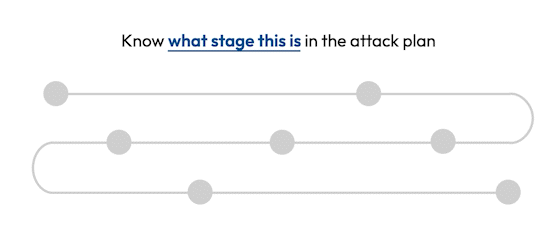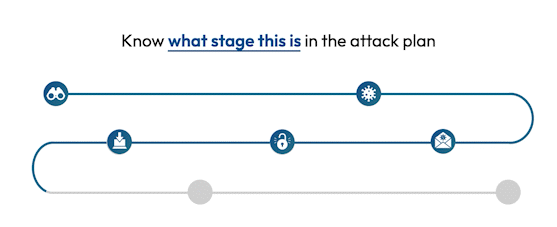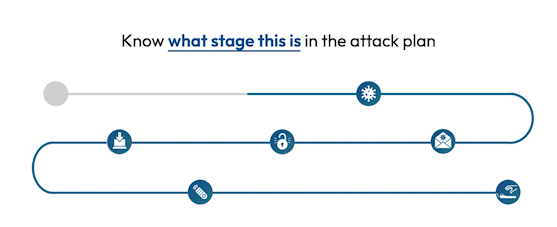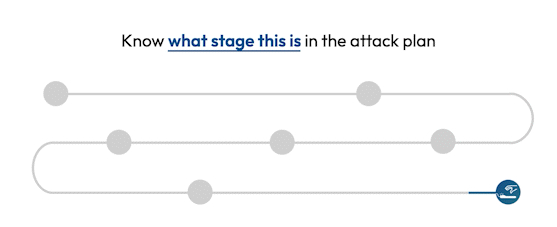
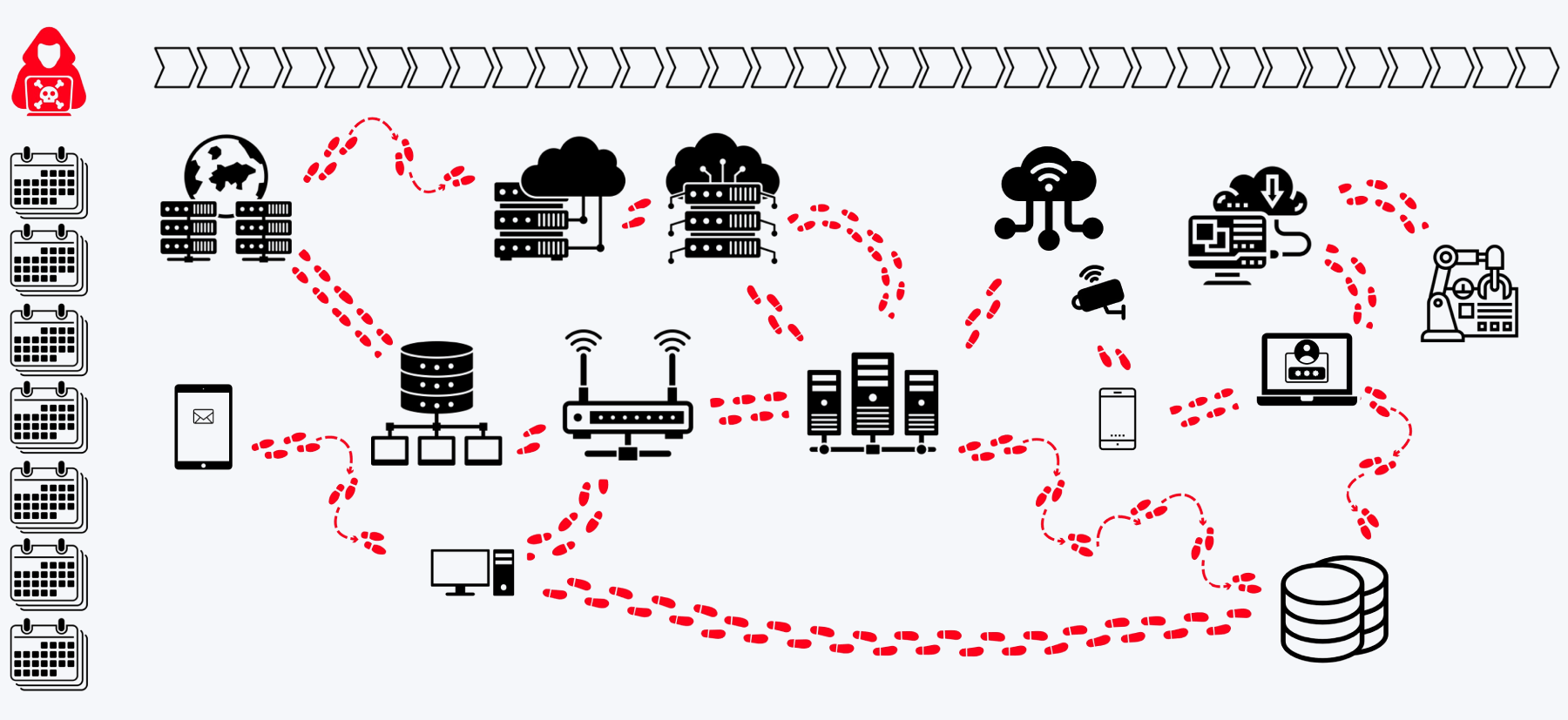
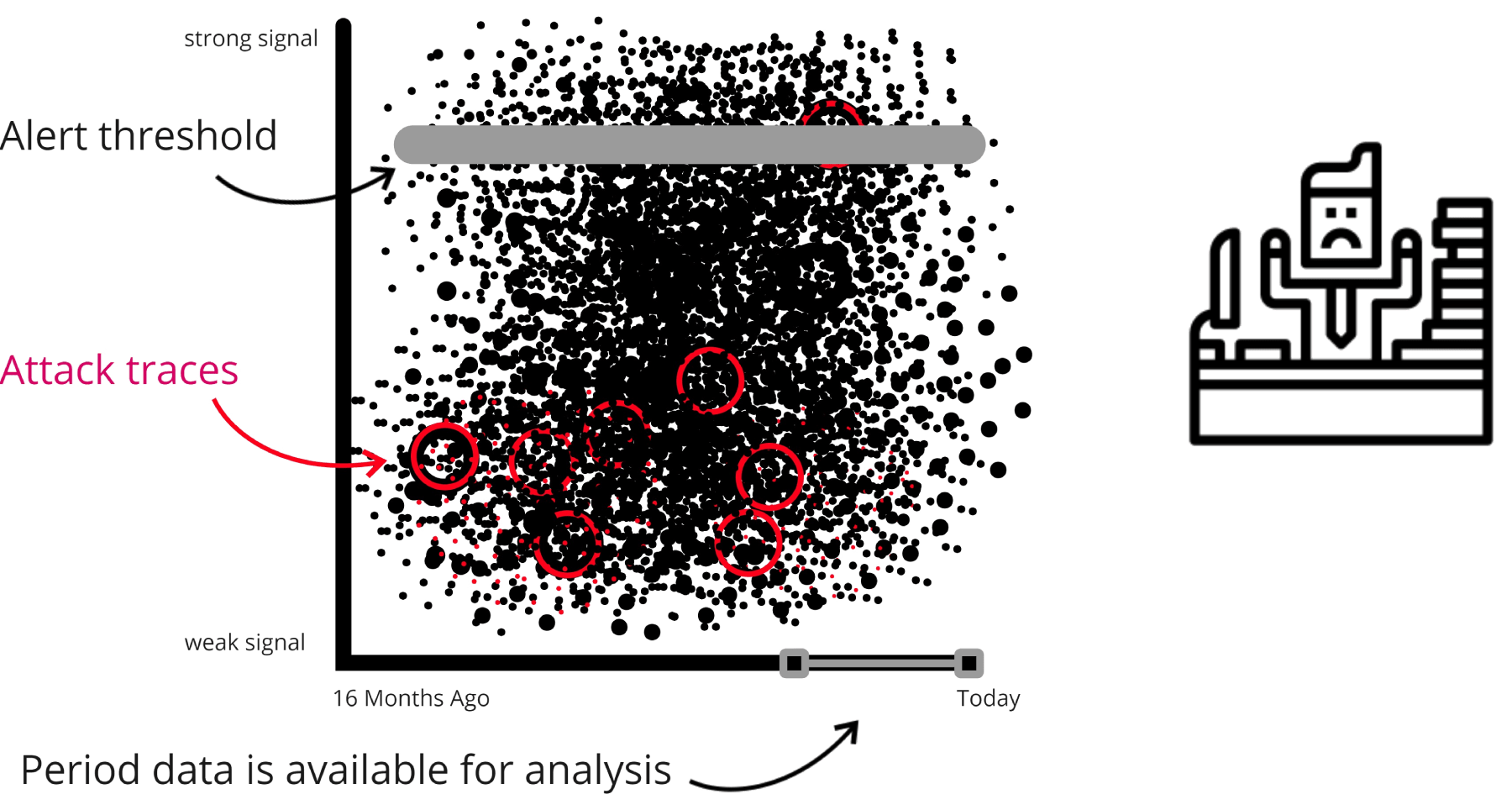
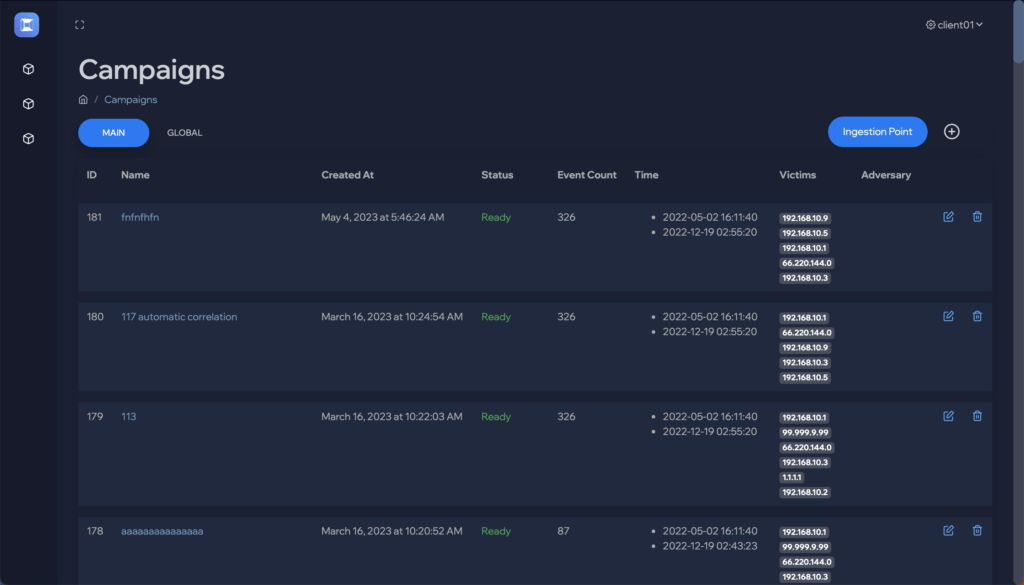
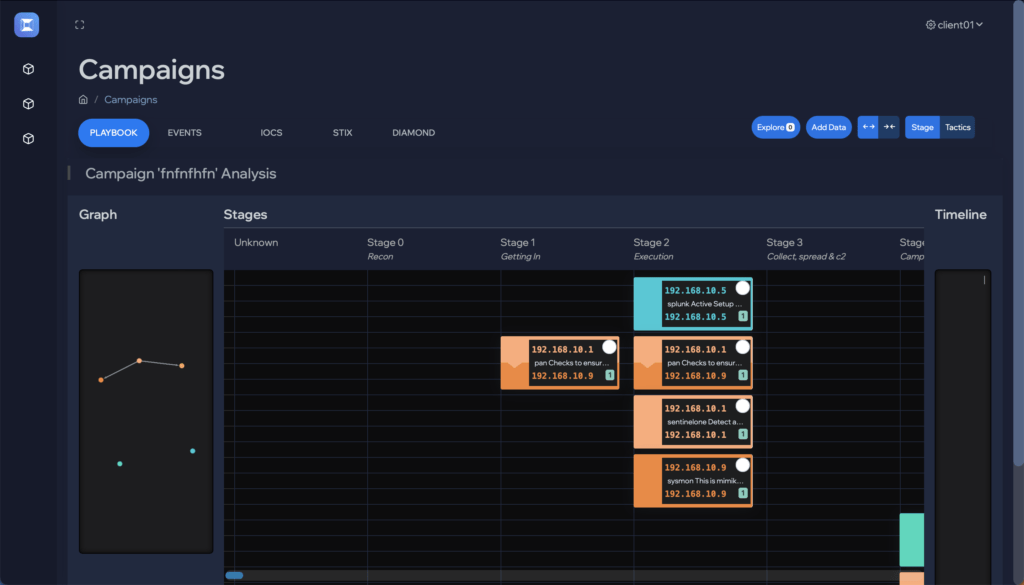
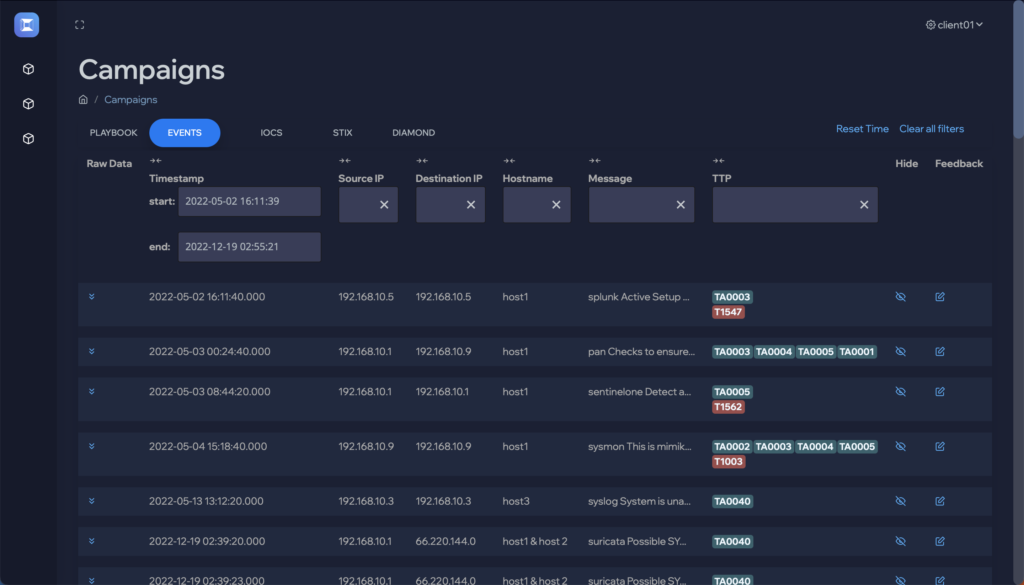
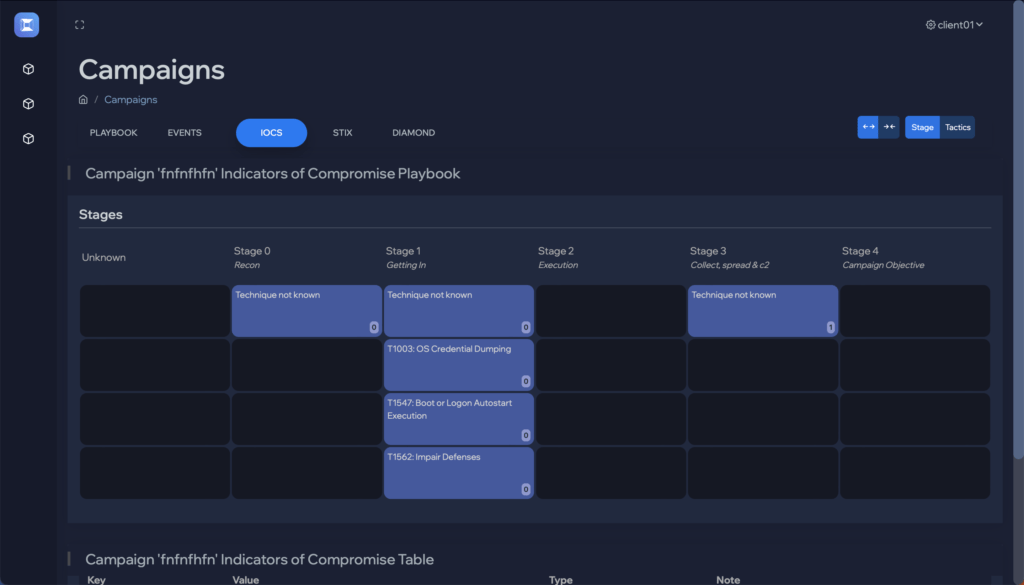
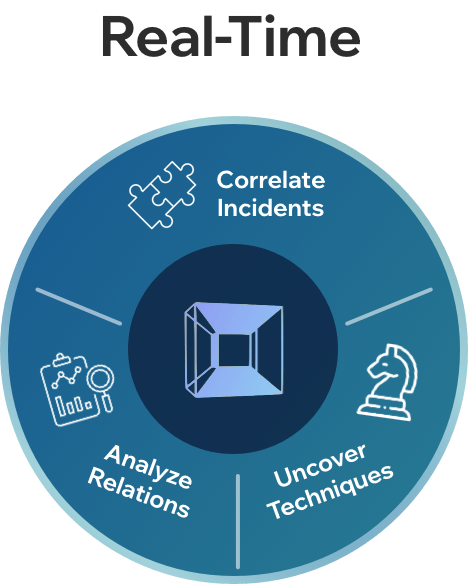
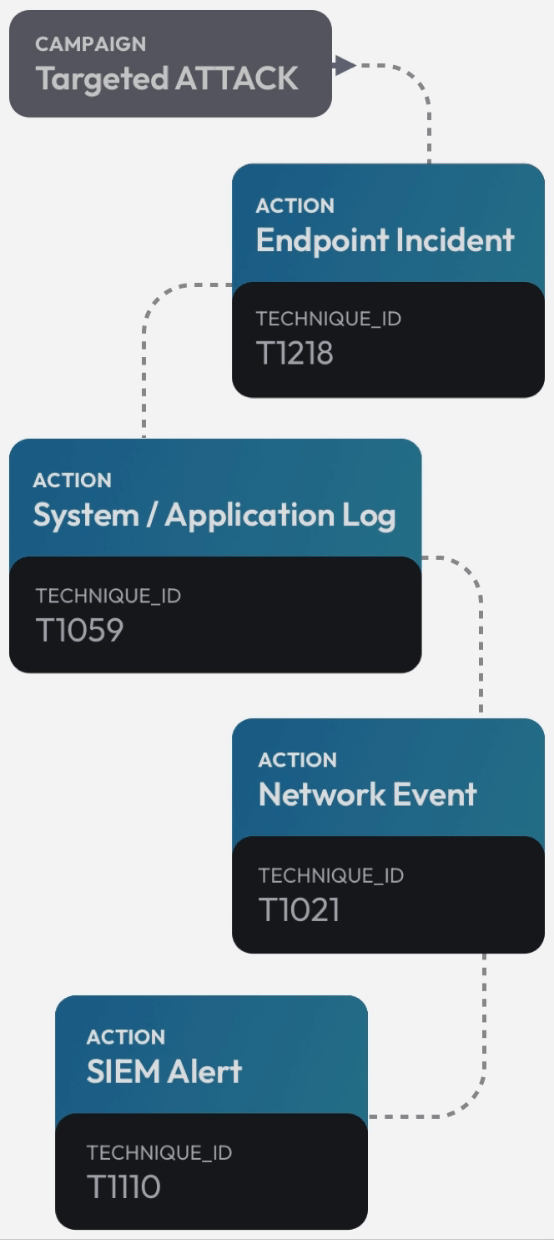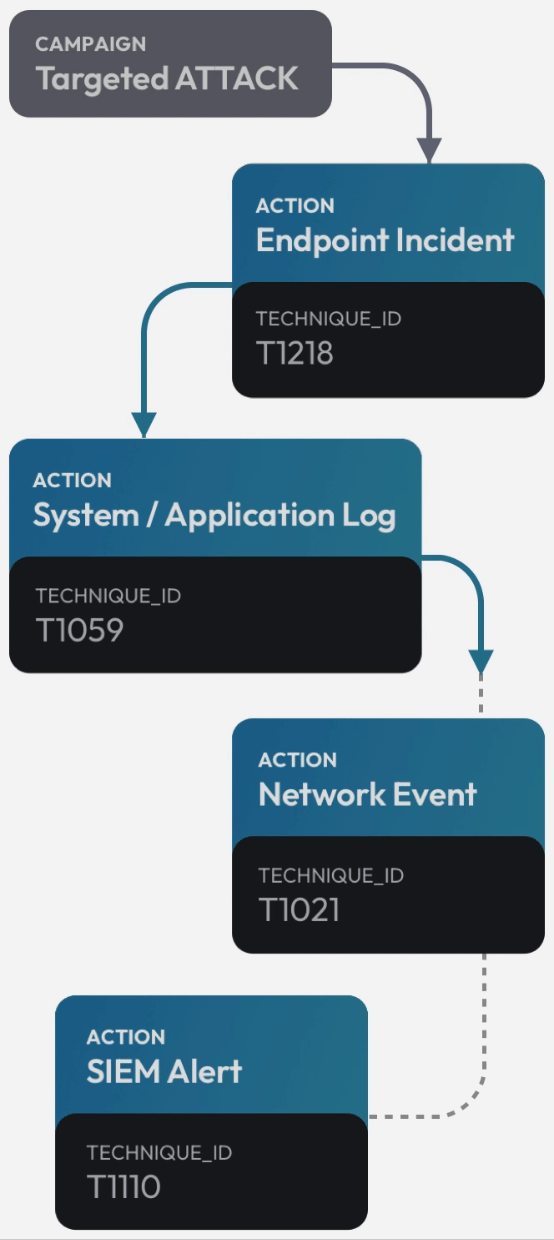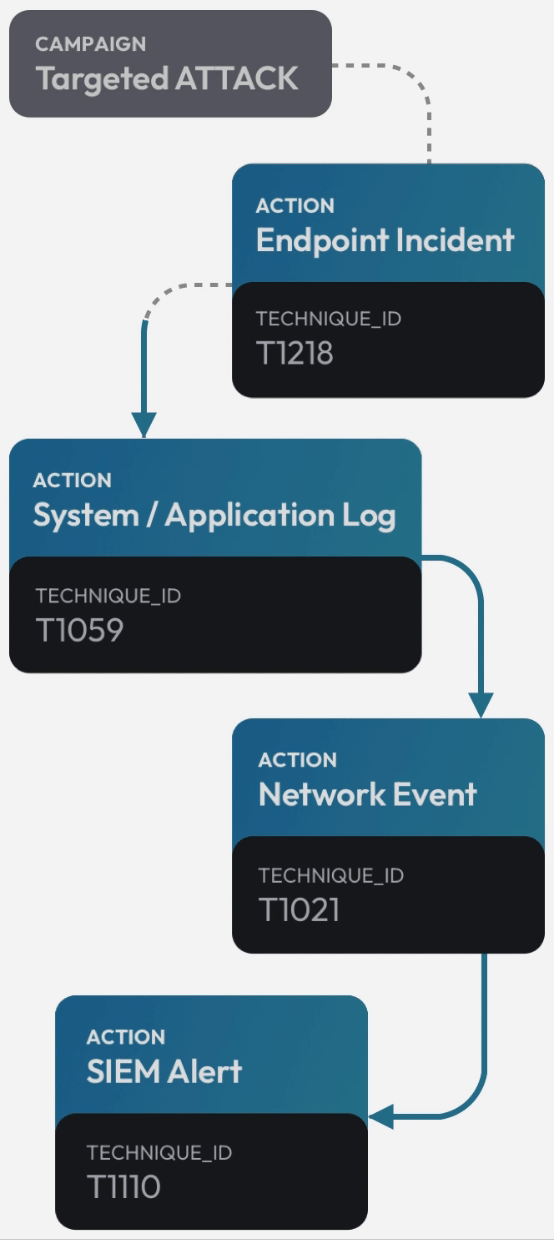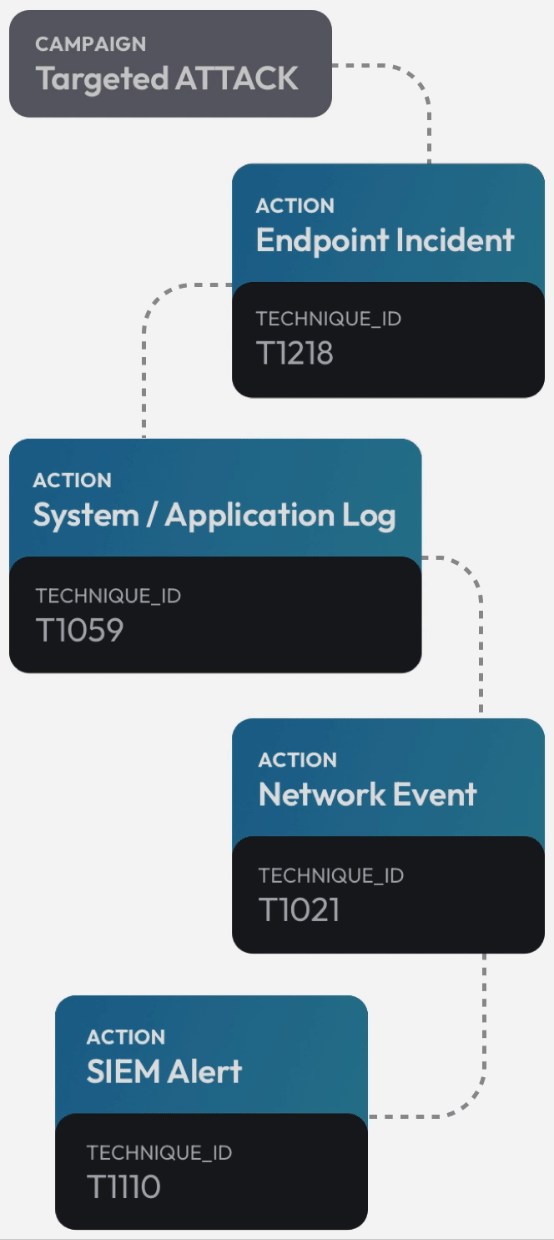
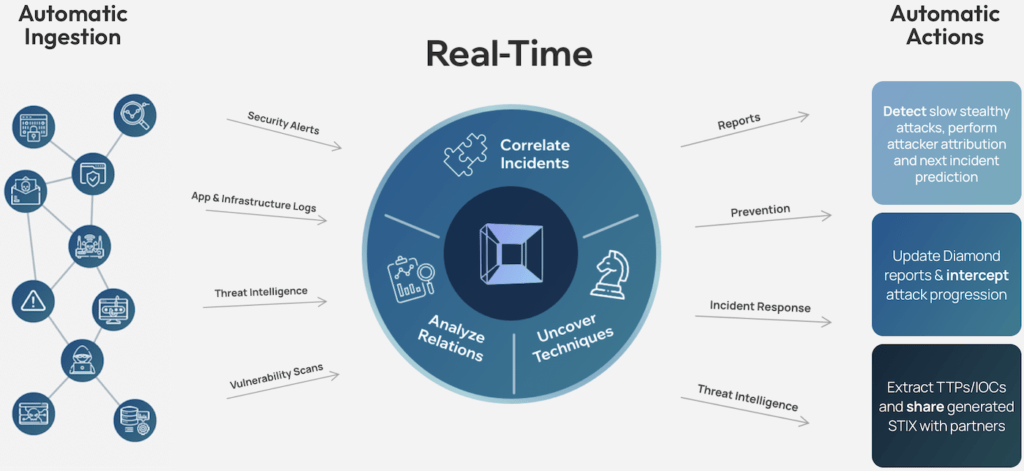
See the attack killchain attack path attack story attack scenario attack campaign attack timeline attack plan attack strategy attack steps attack stages attack progression attack lifecycle attack trail attack playbook in real time.
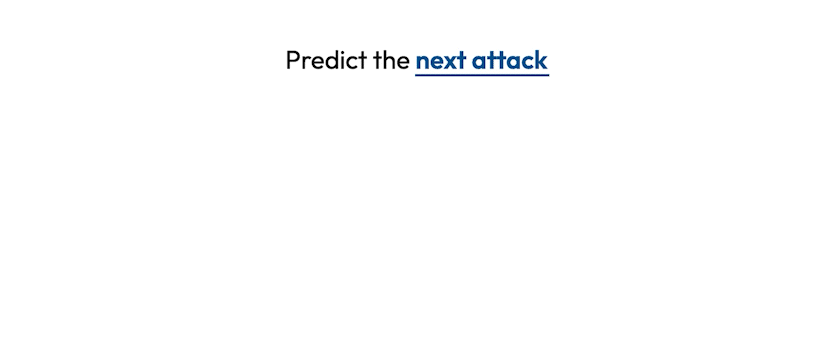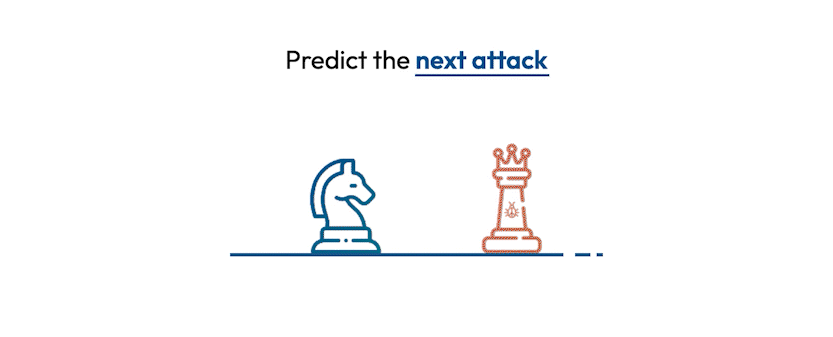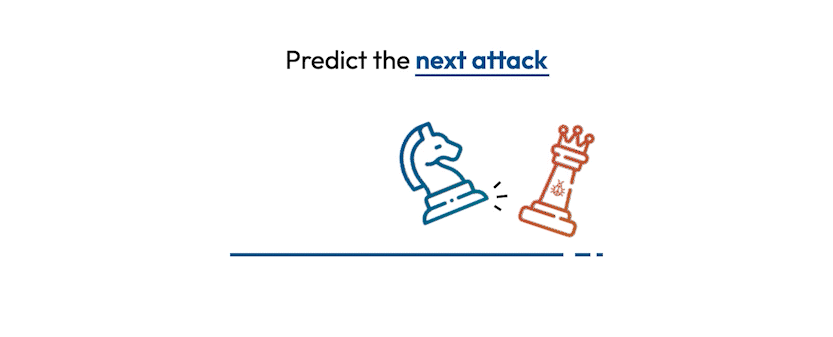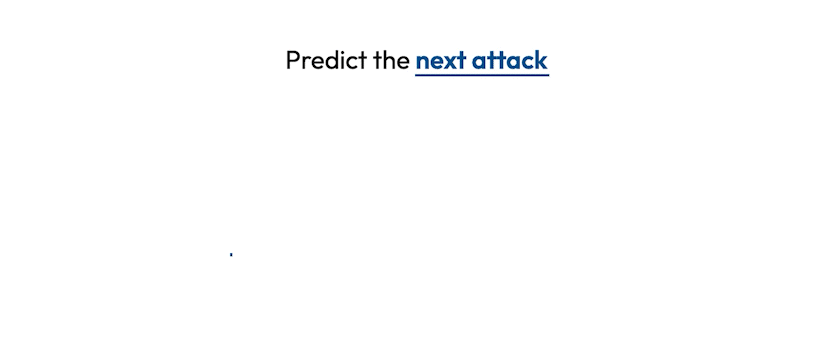
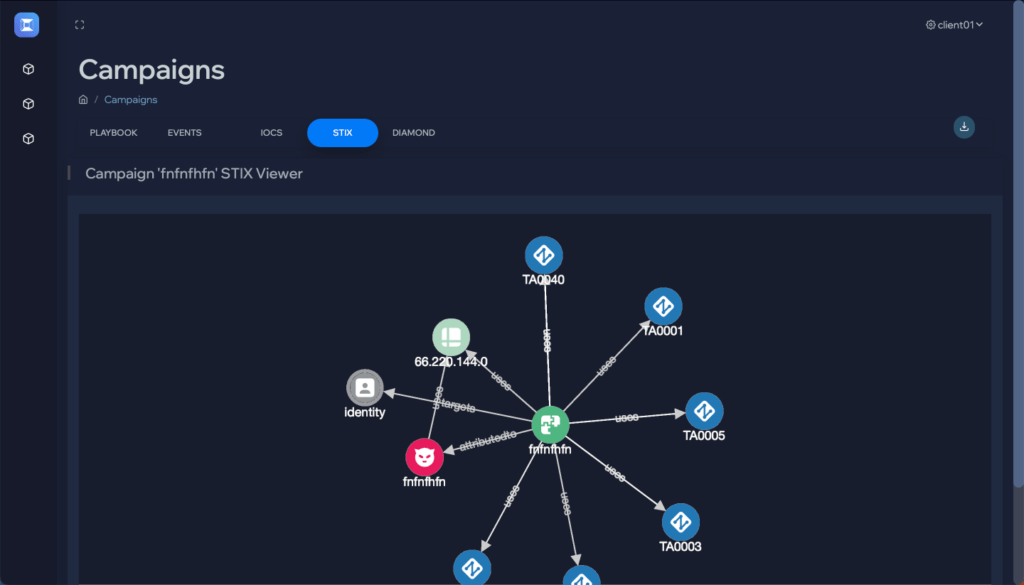
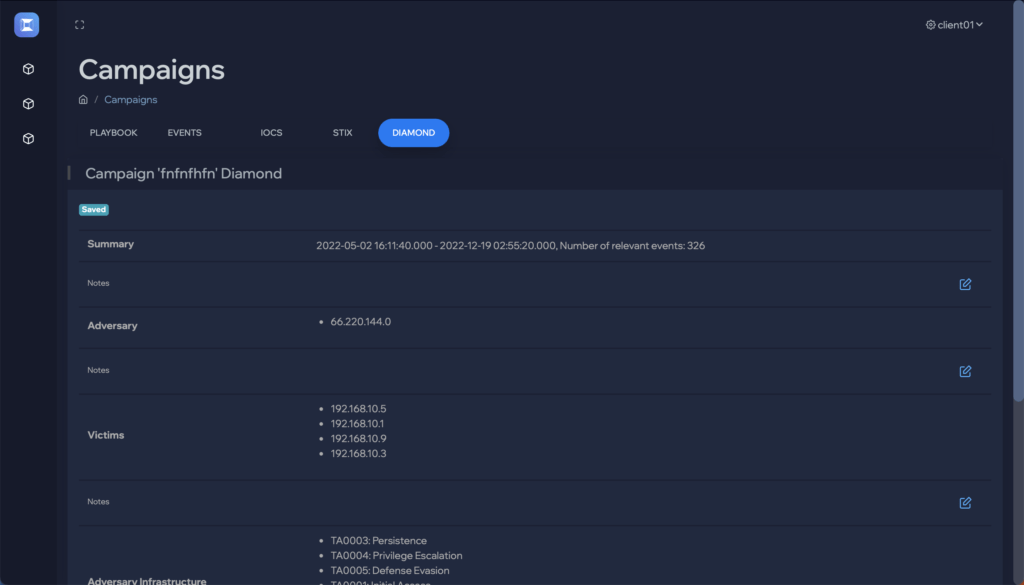
Flip the table, and get the attacker situation-room view of the attack.
Connect dots, correlate signals, see the big picture, and save the day. Today.