The Problem
Inadequate incident correlation contributing to frequent high profile breaches and a soaring cyber crime industry.

Problems with today's
cyber security
A much needed revolution.
Our systems are less secure than those of the 70s, and its getting worse.
On average to detect & contain a breach (IBM)
Increase in unique 0-days exploited (Mandiant)

Average cost of cybercrime for a company (Accenture)
Increase in cyber attacks due to Covid-19 (United Nations)
Attack detection is bloated and ineffective.
in use by security teams (PaloAltoNetworks)
recieved on average by a security team (Forrester)
of attacks generate alerts (Mandiant)
Attackers evade the best detection systems and breach
the most secured organizations.









Attack detection is bloated and ineffective.
in use by security teams (PaloAltoNetworks)
recieved on average by a security team (Forrester)
of attacks generate alerts (Mandiant)
Attackers evade the best detection systems and breach
the most secured organizations.

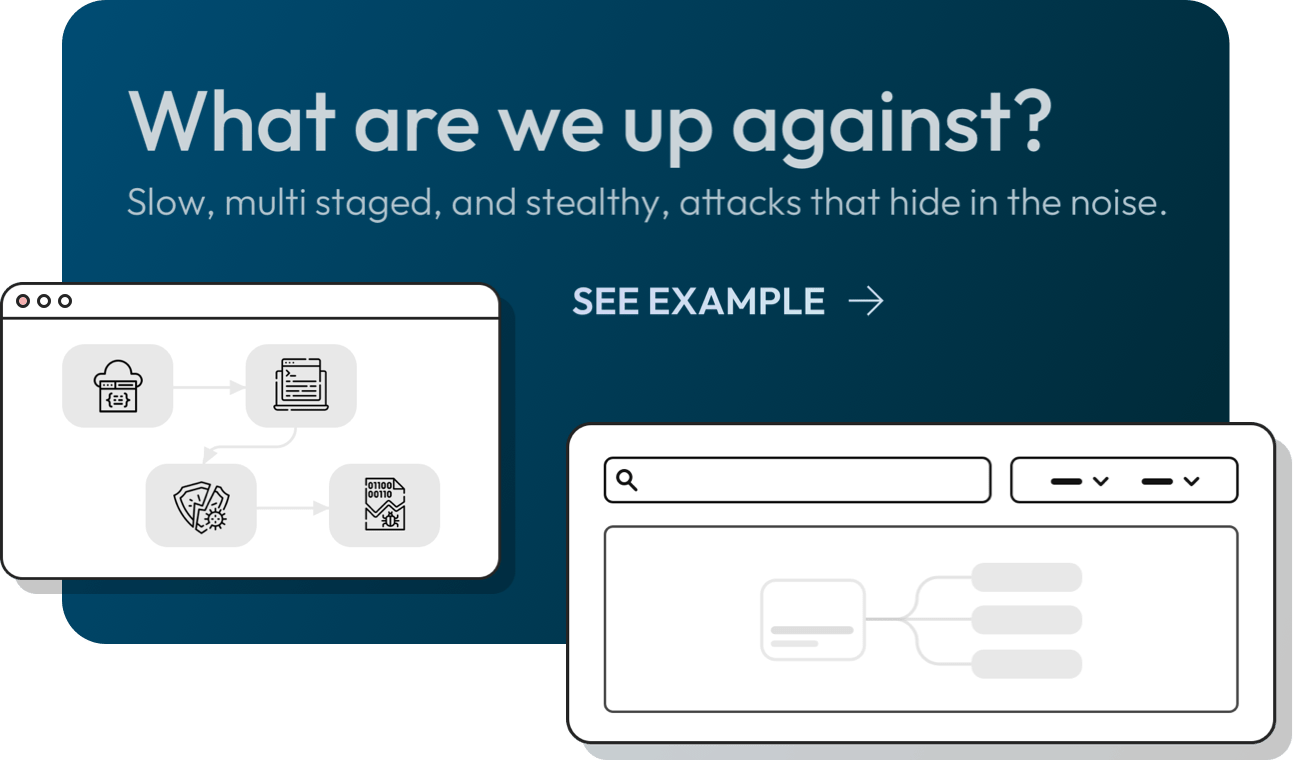
What to blame?
Surveyed in 2022 (SANS), security experts blame 8 fundamental challenges:










On-premise deployment? More than 400GB a day? Custom functions?
What to blame?
Surveyed in 2022 (SANS), security experts blame 8 fundamental challenges:








On-premise deployment? More than 400GB a day? Custom functions?

Horizontally: Attack progression on MITRE ATT&CK Tactics
Vertically: Timeline between Aug 2017 and Aug 2018
As the attack covered multiple networks, data centres, and systems, every machine type is colour coded
SOC team actions
Exfiltration of sensitive data

Automatically correlating signals and traces, to uncover attacker progressions in your organization.
Subscribe Now
Get monthly cyber data science news and insights
©Cypienta. All Rights Reserved.
Engineered by ezSec